Why Automated Sensitive Data Catalog
A common misconception is that IT teams can manually compile a list of sensitive data


Organizations often link the word ‘data’ to value, competitive advantage, returns, etc. Most organizations today are data-driven and data contributes almost directly to the manufacture of products and services. And yet, the word ‘data security’ is equated to terms like risk, penalty, and compliance.
According to a 2017 Forrester report, a little over 60 percent of security professionals aren’t aware of where data resides in their organizations. A study by IDC research found that more than 80% of organizations surveyed contained more than 10 duplicates of each of their database. These amounted to more than 200 million duplicates of the same database which needed to be secured. This is when an efficient Data Discovery tool can help you identify the data that resides anywhere across your data landscape.
Unless an organization is aware of the following, its (confidential) data may not be secure and the organization itself may not be compliance-ready:
-What data is it collecting?
-Where does the data reside?
-How critical is the data to the organization?
-Who has access to the data?
-How is the organization going to use the data?
At the same time, you must also consider which databases require the least to highest levels of security. This decision on database security can be made based on the sensitivity of the data. A well-equipped data classification tool can help you classify data according to its sensitivity which allows you to strategically align your privacy and security requirements.
What is Data Discovery?
Data Discovery is the process of identifying data across your organization’s data landscape. Within the context of Sensitive Data Security, Sensitive Data Discovery is a process generally accomplished by software or solutions that scan multiple or all data sources across your enterprise. These solutions can be comprehensive Sensitive Data Loss Prevention, monitoring, data vulnerability scanning, and privacy compliance solutions such as Kogni. Kogni scans your entire data landscape for (sensitive) data so that no location is left hidden or forgotten and secures the data so that no data is left vulnerable to outsider or insider threats.
How does the manual data discovery process work?
-A manual data discovery process starts with organizations defining what they consider sensitive data. Sensitive data differs across industries. For a healthcare firm, its patient’s medical records can be one of its most critical data while a financial organization may consider its customer’s credit card as sensitive information.
-The second step in the process is to list down all the locations that may contain sensitive data. Data sources such as email, BYOD, cloud, local data servers can be part of this list.
-In the final step, organizations must decide what needs to be done with sensitive data based on its degree of sensitivity. The data either needs to be secured, erased, or monitored- all of it manually!
An automated Data discovery solution can do all this and more. Apart from discovering, classifying, and securing sensitive data, it can also continuously monitor for any possible anomalies, scan for vulnerabilities and fast-track the compliance process.
What is Data Classification?
Data Classification enables you to tag the identified sensitive data with the right degree of sensitivity.
Organizations classify their data under four labels-
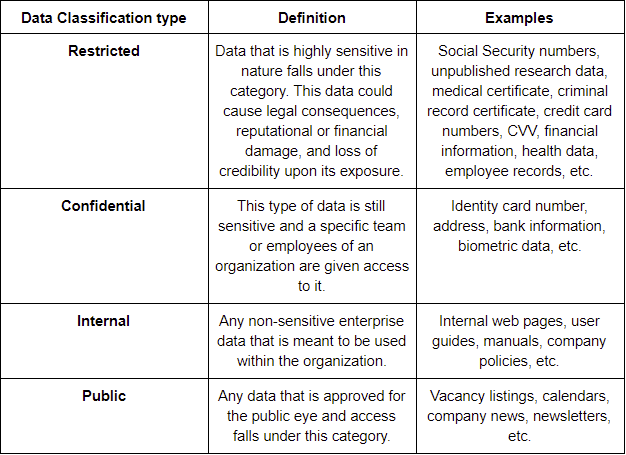
Significance of an automated Data Discovery and Classification tool:
The disadvantages of manual data discovery and classification process outweigh the advantages of the automated system. While a manual process might cost lesser than the automated one, the accuracy, vulnerability scanning efficiency, and timely output of the automated process heavily compensate for it.
An acclaimed, purpose-built data discovery and classification tool can perform the following functions:
-Discover hidden, unknown and rogue databases
-Scan for data vulnerabilities
-Identify sensitive data from across the organization’s data landscape
-Classify data based on its sensitivity
-Automate both data discovery and classification across the enterprise
-Accelerate data compliance efforts
There are plenty of organizations that spend a fortune on perimeter security and fail to realize that their data needs to be equally secured too. Incidents like insider threats cannot be prevented with efficient perimeter security alone. You need an efficient data security system with inbuilt data discovery and classification features that can detect any abnormalities in the data access patterns.
Tesla, in Jan 2020, filed a lawsuit against its former employee for altering company codes and transferring highly confidential company information to unknown third parties. The employee managed to make changes to Tesla’s Manufacturing Operating System’s source code to export gigabytes of data to third parties.
Year after year, we see such cases coming out frequently. Incidents of insider threats originate from employee/third party negligence, an upset employee looking for a chance to get back at the company, or in the above case, an employee with ready access to sensitive data. If perimeter security is your organization’s door, employees with access to sensitive data are the key to that door. Without a Data discovery and classification tool alerting you on abnormal access patterns, your door is almost always open. With such an evolved system, you can achieve the following:
-A comprehensive security solution with data at its core: When you are aware of what data your organization contains, its nature of sensitivity, and where all that data resides, you are on the right track to achieving an effective data security solution. When you know which data or database requires most of your attention and demands encryption, you can react to insider threats more efficiently.
Kogni is an efficient Data discovery and Classification software that lets you discover and classify your sensitive information according to predefined or custom-made tiers of sensitivity.
-A system that monitors access patterns: Once you classify sensitive information, you will need to grant employee access to this data. It is always recommended to limit access to your most sensitive data to the least number of employees. An industry-acclaimed data classification system monitors access patterns and requests at all times and alerts you in case of an access violation or a deviation in the pattern.
Kogni, backed by a carefully architected AI-centric model studies access patterns and instantly notifies you should a deviation occur. This exercise lets you proactively identify insider data threats and stop them from turning into full-blown data breaches.
-A system that accelerates data compliance: Regulations such as CCPA, HIPAA, GDPR, and others require that you are aware of
-where sensitive data is located in your organization’s landscape
-who has access to it
-if and how it is being altered, etc.
Without a data discovery solution such as Kogni pointing out the whereabouts of your sensitive data and how much of it resides in each database, you may not be able to comply with mandatory privacy regulations. Compliance may also not be achievable without a data classifier informing you which data falls under the “highly sensitive data” category.
How can Data discovery and classification make you compliance ready?
Below are a few key requirements under HIPAA, GDPR, and CCPA that Kogni can help you comply with. Kogni can accelerate compliance with all the requirements under these three regulations and other local and international data privacy mandates.
-One of the key requirements under HIPAA is Access Control. According to it, a covered entity must execute technical policies that limit access to ePHI to authorized personnel.
Kogni’s data discovery feature discovers all the HIPAA-related sensitive data regardless of their location. Its Data classification tool then classifies the data under preset groups created by Kogni or custom groups created to suit your entity’s unique needs. It makes identifying the data location simple at any given point of time by adding tags to your data and mapping it across users, folders, and permission. May the PHI/ePHI (Protected Health Information/electronically Protected Health Information) be in a database, filesystem, No-SQL, Big Data, or anywhere across the enterprise’s data landscape, Kogni helps locate it in no time. Kogni also supports data in various formats like structured, semi-structured, and unstructured.
Kogni monitors both data at rest and real-time data no matter where they reside and offers unified single-pane visibility to your data. It is also uniquely positioned to identify and report on your critical data that reside in Saas (Slack, Jira, Salesforce) and other hosted services.
-Another important requirement under HIPAA is implementing Integrity Controls. To validate HIPAA compliance, a covered entity must have in place the required policies to ensure its ePHI is not improperly handled or destroyed.
Kogni helps the entity architect a robust analytics process. It tracks HIPAA-related data’s activities like location, state, alterations it goes across your entity’s data landscape, its interaction and activities when in cloud environments, etc. It then logs the potential threats attached to the PHI/ePHI and notifies by sending out appropriate alerts.
Kogni alerts users
-when an authorized user accesses the ePHI from a different geographic location
-when they interact with a never-before-accessed HIPAA-related information
-when they log in from a system that does not have the required client-based certification or when in an unsafe network zone
A common key clause under GDPR and CCPA gives customers the right to know what data/information is being collected and processed online. Under this clause, customers are given the right to access their personal data. They can request and receive a copy of their personal information collected by a firm. They can also receive certain information about how the firm processes their information
Kogni can help organizations comply with this clause. Anytime a consumer requests to access their data, organizations leveraging Kogni’s powerful data discovery feature can pull up the data instantly from all available data sources.
- Another key clause common to CCPA and GDPR offers customers the right to opt-out of businesses selling/reselling customers’ personal data. This clause allows customers to opt-out of their data being processed for marketing purposes. They can opt-out of their information being sold to third-party sales that support marketing activities.
Organizations can access all the data belonging to a particular customer with a few clicks when using Kogni’s efficient data discovery feature. The requested data gets pulled up in an instant on the screen which helps process the customer’s request. Organizations can accordingly inform their third-party organization to stop processing your customer’s data.
- An important clause under GDPR and CCPA dictates the customer’s right to Deletion/Erasure. A customer can request for the erasure of their personal data under this clause. Businesses must also inform other businesses (third-party data controllers) that process such data to ensure complete deletion of the information.
When a customer initiates their right to deletion, organizations can use Kogni’s effective data discovery solution to instantly collect their data from all available sources and comply with this clause well ahead of the stipulated duration.
Kogni’s uncomplicated and cost-effective Data Discovery and classification solution is easy to implement and is a comprehensive approach to your Data Security strategy. With Kogni, you can significantly reduce the time you spend on discovering and classifying your sensitive data. Leave it to Kogni to efficiently automate your Data Discovery, Classification, Security, and Compliance!