
Data security in the Education Sector [https://unsplash.com/photos/OyCl7Y4y0Bk]
Unauthorized access to a web application cost the Personally Identifiable
Information (PII) of around 1.3 million faculty members, staff, students,
applicants,

An extremely popular New York-based Entertainment and Media Lawyers’ firm-
Grubman Shire Meiselas & Sacks, fell victim to a ransomware attack in May 2020.
The attackers demanded a huge ransom of over $20
The Zero Trust Security Model was conceptualized in 2010 by John Kindervag,
principal analyst at Forrester Research Inc. As he defines it, Zero Trust is an
IT security model that requires strong authentication

Many of the recent data breaches were detected too late. Consider Equifax data
breach:
* "More than 145 million Americans were affected by the Equifax hack last
summer. The personal information accessed included
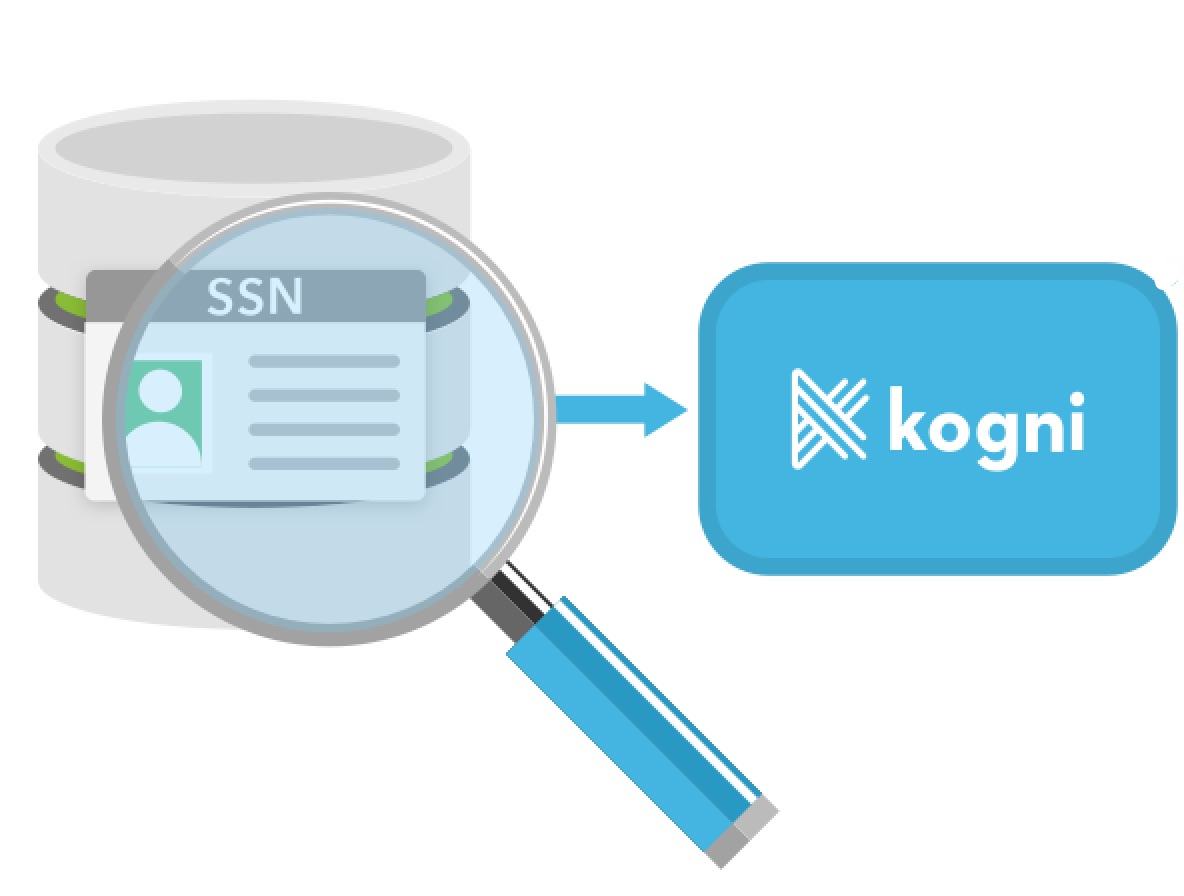
A common misconception is that IT teams can manually compile a list of sensitive
data locations. However, manual sensitive data discovery is impractical for the
following reasons:
* In traditional relational databases such as

(1) The GDPR only applies to companies with physical presence in EU.
Fact: The GDPR applies to any company that handles the personal data of EU
residents, even if the company has no






